Viewing Audited Events
To help administrators keep track of various events, Security for Confluence places entries in Confluence’s Audit Log.
Accessing the Audit Log
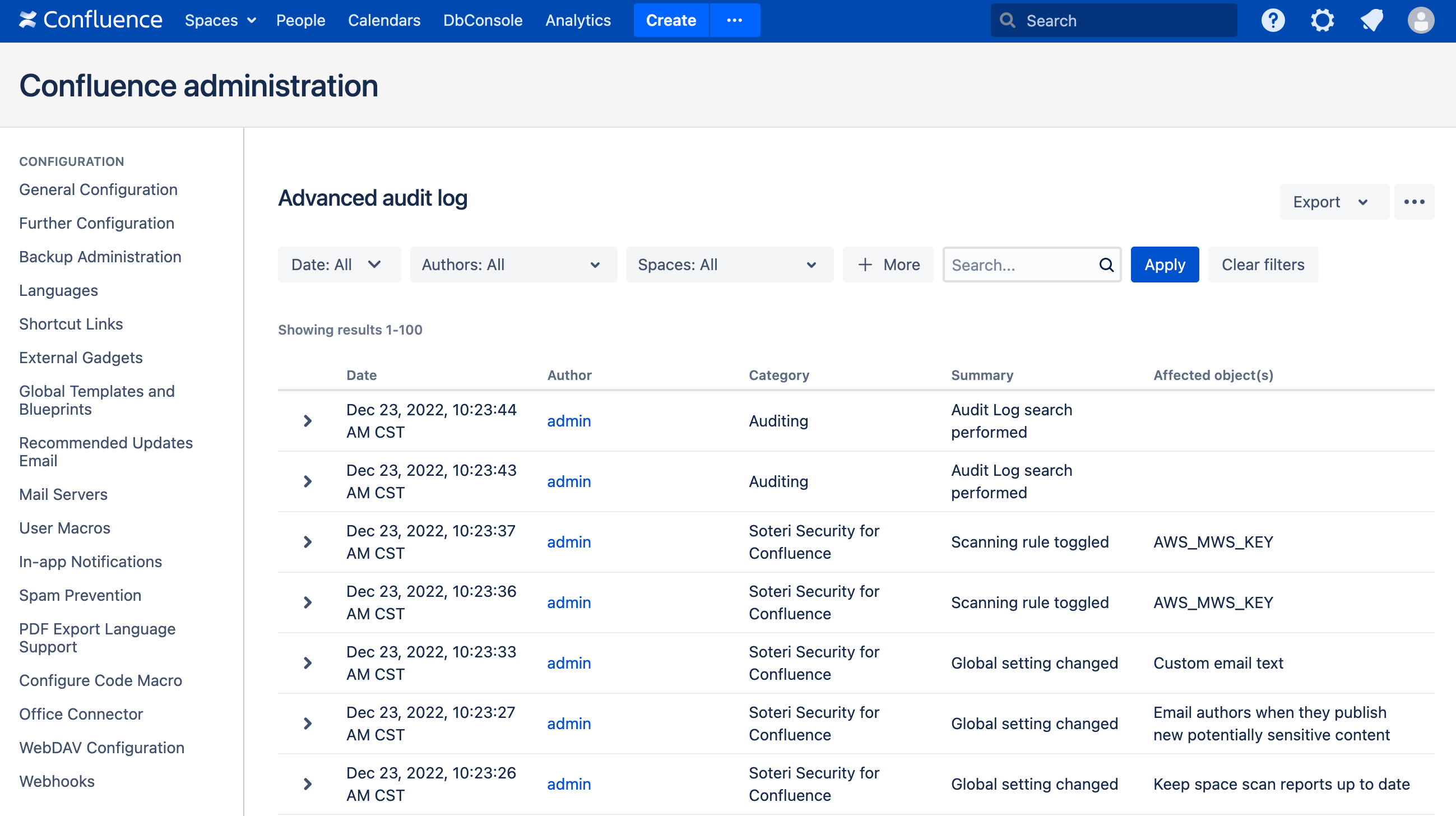
From the Confluence administration page, select Audit log (under “Administration”) from the sidebar. This brings up the “Advanced audit log” page:
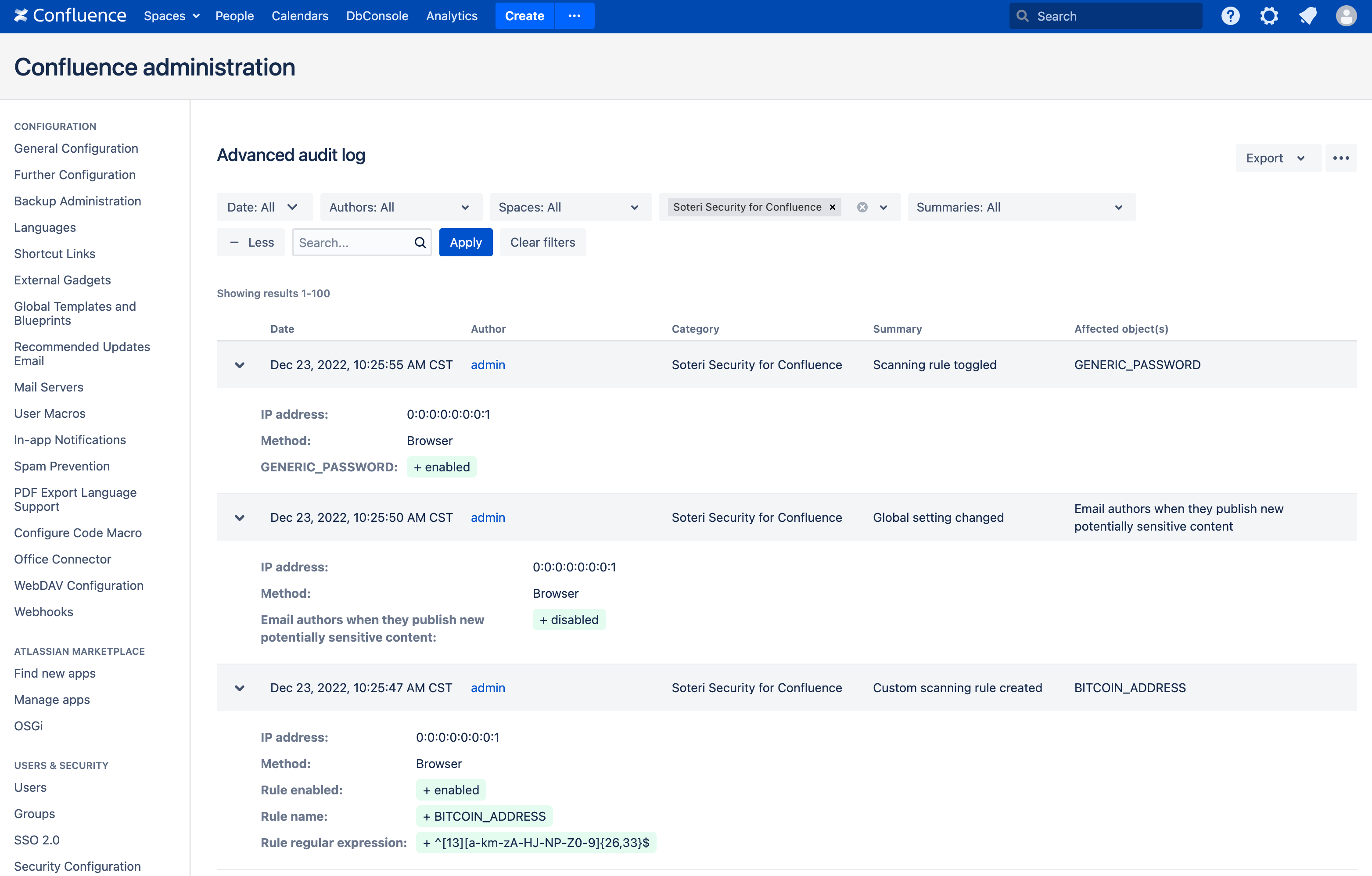
From here, click on the + More button. A new Categories drop-down will appear. From that, select “Soteri Security for Confluence” to view only Security for Confluence audit log events. You can expand events to see more details:
Confluence audit log access is only available to Confluence Administrators.
Audited Events
The following Security for Confluence events are currently recorded in the audit log:
Audit Event Category | Description |
|---|---|
Scanning rule toggled | When a user toggles a built-in rule. |
Global setting changed | When a user changes a setting on the settings page. |
App administrator setting changed | When a user or group is added or removed from the list of users and groups with explicit app access. |
Custom scanning rule created | When a user creates a new custom rule. |
Custom scanning rule updated | When a user changes a custom rule. |
Custom scanning rule deleted | When a user deletes a custom rule. |
Notification email sent: potentially sensitive content | When a notification email is sent due to potentially sensitive content being published. |
User edit introduced potentially sensitive content | When a user edit introduces potentially sensitive content. This includes new and edited pages, blog posts, comments, and attachment uploads.
|
Scan finding reviewed | When a user marks a scan finding reviewed. |
Scan finding reviewed individually | When a user marks a scan finding reviewed for the specific page, comment, or attachment. |
Scan finding un-reviewed | When a user unmarks a scan finding reviewed. |
Scan finding un-reviewed individually | When a user unmarks a scan finding reviewed for the specific page, comment, or attachment. |
All scan findings un-reviewed | When a user unmarks all findings reviewed for a space. |
All individual scan findings un-reviewed | When a user unmarks all individual findings reviewed for a specific page, comment, or attachment. |
Content scan triggered | When a user triggers a scan of a specific piece of content. |
Space scan triggered | When a user triggers a scan of a specific space. |
Whole instance scan triggered | When a user triggers a scan of the entire instance. |
Scheduled scans canceled | When scheduled scans are cancelled by a user. |
Dashboard overview exported | When a user exports the dashboard overview. |
Findings exported | When a user exports findings for a specific space. |
All findings exported | When a user exports all findings. |
False positives exported | When a user exports reviewed findings for a specific space. |
All false positives exported | When a user exports all reviewed findings. |
Attachment scan information exported | When a user exports scanned attachment information for a specific space. |
All attachment scan information exported | When a user exports all scanned attachment information. |
Globally reviewed false positives exported | When a user exports globally reviewed false positives. |
Globally reviewed false positives changed | When a user changes globally reviewed false positives. |
Cancelled exports | When a user cancels running exports. |
REST API
Confluence provides a REST API for accessing all audit log events. For instance, you can fetch recent audit events with a REST API call that looks like this:
curl -u admin https://{confluence.server}/rest/api/auditReference the REST API documentation for your Confluence version for more information.
External Integration
The Confluence audit log can be integrated with external SIEM tools (like the ELK stack) to do things like notify administrators when Security for Confluence settings are changed, or potentially sensitive content is published. Reference Atlassian’s Guide to audit log integration for more information.